As more businesses grow online, the need for strong security measures grows right along with it.
- The 2022 Cybersecurity Almanac from Cybersecurity Ventures says that from 2021 to 2025, the world will spend a total of $1.75 trillion on security measures.
- There are many different kinds of cyberattacks, but the most common ones that hurt many companies are social engineering attacks like phishing and denial-of-service attacks.
- Using strong passwords and having up-to-date antivirus softwareare just some of the things you should do as part of an overall cybersecurity best practices.
- Every second, more than 159TB of internet traffic is generated, according to Internet Live Stats. As a result, today's businesses are vulnerable to cyber malcontents seeking to derail businesses through theft and disruption.
You may not know when an attack could occur but taking proper precautions can hamper or completely stymie a hacker’s attempt to access your network.
In light of this, Softline and Microsoft co-organized an event on August 11, 2022, with the topic "Protect your business with end-to-end security solutions" that focused on why your business may be vulnerable to a cyberattack and how to avoid a compromising situation by implementing cybersecurity best practices.

After three years of the COVID outbreak, this is the first offline event and it was more successful than expected with 42 attendees from different companies across the country.

Over the course of a 5-hour session, Softline raised awareness of the importance of security in organizations by presenting in depth and engaging in a lively discussion with the audience, led by Softline Security Experts - Mr. Chhoem Dara, a Security Technical Specialist, and Mr. Sang Pham, a Security Practice Lead APAC.


According to the speakers, businesses must improve productivity while also dealing with numerous challenges. An endpoint in the remote work environment, for example, can easily be infected by personal email, USB, and other vectors.
On the other hand, malware on the endpoint enables an adversary to steal or damage files and systems.
As a result, businesses must improve both productivity and security simultaneously. It’s a delicate balance between productivity and security.
In today’s event, attendees also had the opportunity to learn that attackers are always looking for vulnerabilities in organizations’ identities, data, devices, and infrastructure.Because of these vulnerabilities, cyberattacks and scams such as phishing and ransomware are increasingly targeting many businesses.

Besides, in this event, weintroduced an end-to-end security solution from Microsoft to protect your business across the attack kill chain:
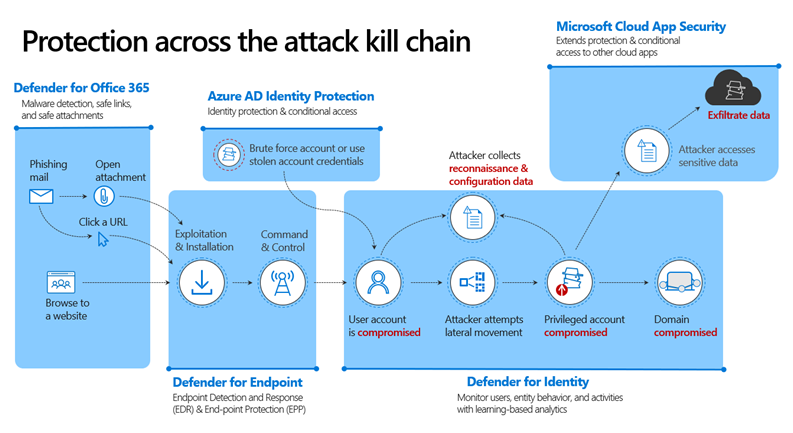
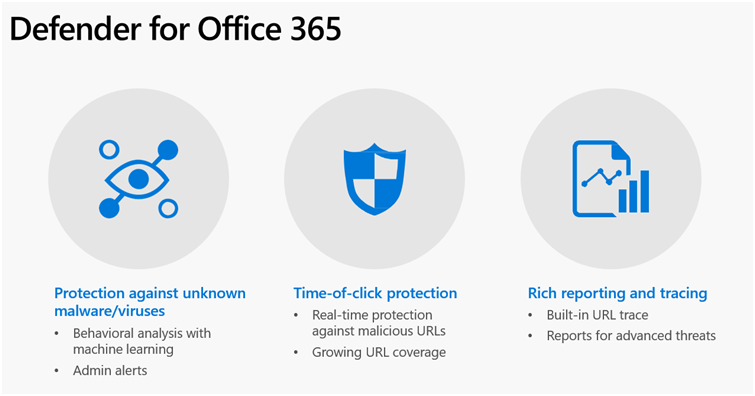
Defender for Office 365 – Malware detection, safe links, and safe attachments:
- Improve your security against zero-day attacks by directly integrating into OneDrive for Business, SharePoint Online, and Teams.
- Protect your users from malicious links within shared documents in OneDrive for Business, SharePoint Online, and Teams.
- Safeguard your environment by blocking malicious content identified by ATP.
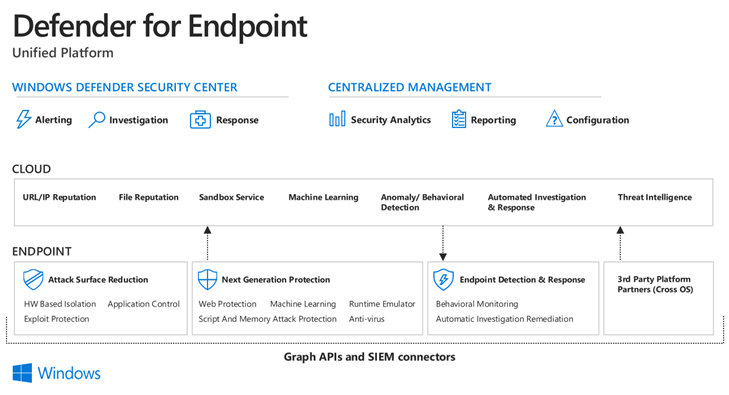
Defender for Endpoint – Endpoint Detection and Response (EDR) & End-point Protection (EPP):
- Detect, investigate, and respond to advanced attacks.
- Unify from the Windows Defender Security Center and Centralized Management.
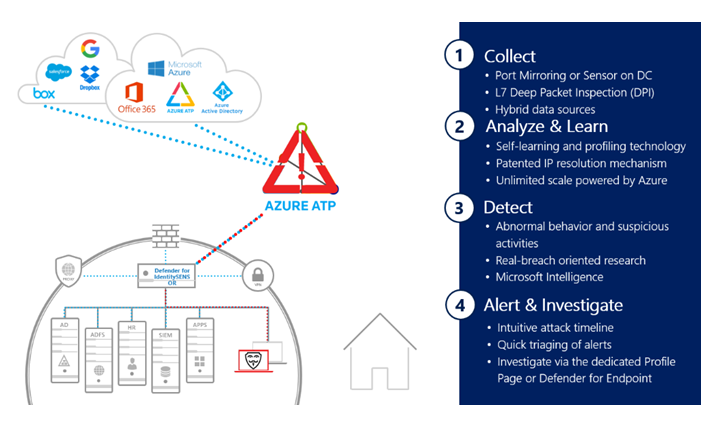
Defender for Identity – An essential part of protecting the entire enterprise:
- Prevent, detect, investigate, and respond to compromised users and lateral movements in on-premises environments.
- Monitor users, entity behavior, and activities with learning-based analytics.

Azure AD Identity Protection – Identity protection & conditional access:
- Automate the detection and remediation of identity-based risks.
- Investigate risks using data in the portal.
- Export risk detection data to your SIEM (security information and event management).
Microsoft Cloud App Security – Extend protection & conditional access to other cloud apps:
- Cloud Discovery – Discover 14K+ cloud apps in your environment, gain visibility into shadow IT and assess risk.
- Information Protection –Shape your cloud environment with granular controls and use out-of-the-box or custom policies for data sharing, and data loss prevention.
- Threat Protection – Identify high-risk usage and cloud security issues, detect abnormal user behavior, and prevent threats.

This is a complete solution that businesses can use to improve their cybersecurity and lower the chance of falling victim to a cyberattack or data breach.
It's also important to note that businesses in heavily regulated industries, like healthcare or finance, shouldn't be the only ones to take cybercrime seriously. Every business, no matter how big or small, needs to put a cybersecurity program at the top of its list of priorities, as cybercriminals do not discriminate.
Finally, we'd like to thank you, Microsoft Cambodia, for co-organizing the event with us, as well as everyone who attended. We will hold more events like this in the future to help you improve your cybersecurity.

Contact Softline to get the webinar recording and detailed support!
Contact information:
T: +855 23 99 00 39
E: info@softline.com.kh
